
Cyber threats lurk in unsuspecting corners, often showing up in surprising ways that can leave companies scrambling to protect their brand and integrity.
One such threat is Dangling DNS. Although not a new phenomenon, this vulnerability is gaining traction as an easy avenue for hackers to inflict serious damage. As companies become more reliant on digital infrastructure and subdomains for various services, the risk only increases. Let’s look into what Dangling DNS is, how it can be targeted, and more importantly, how you can protect your brand against it.
What is Dangling DNS?
Dangling DNS records occur when a subdomain points to a service that no longer exists. Companies often delegate subdomains to third-party services or cloud providers; however, when these services are terminated or moved, the DNS records can remain unchanged, pointing to non-existent services. This oversight creates an exploitable vulnerability that can lead to a subdomain takeover by cybercriminals. By registering the domain name of these abandoned spaces on these third-party services, cybercriminals can seize control of the subdomain. This may allow them to send fraudulent emails, launch phishing campaigns, and conduct impersonation attacks targeting your company’s customers, employees, or partners. Such attacks can severely damage your brand’s reputation and erode trust. The scariest part is that this exploit can be enacted without raising obvious red flags, making it an elusive threat demanding vigilant monitoring.
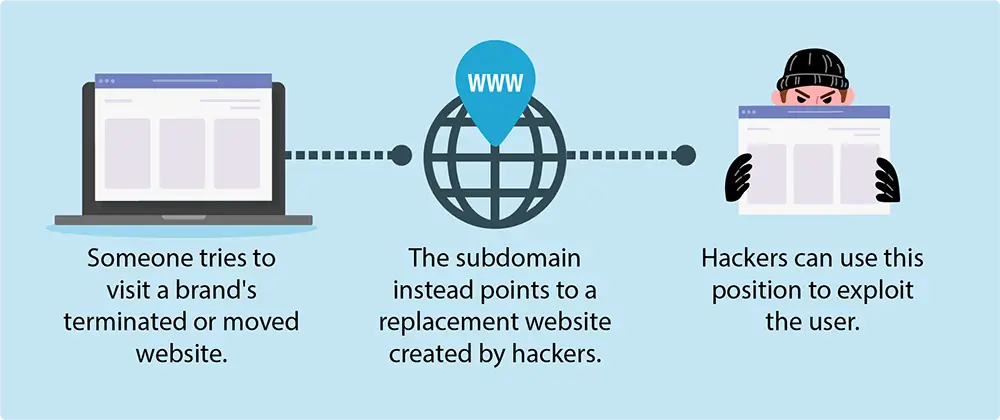
The Growing Danger of Dangling DNS
The growth of cloud services and digital transformations has led companies to rapidly spin up new subdomains, often without comprehensive tracking and decommissioning processes in place. As these infrastructural web components grow, so does the attack surface available to hackers.
The potential for wide-scale phishing attacks increases exponentially as hackers manipulate these ‘dangling’ subdomains to lure in unsuspecting customers or partners. In doing so, they can harvest credentials, identities, and sensitive information – leaving the original, legitimate companies to bear the brunt of reputational damage and customer mistrust. This amplification of risk illustrates why dangling DNS is a threat that no business, no matter the size, can afford to ignore.
What you can do about it
1. Create a Security-Conscious Culture
Since many attacks such as phishing attempts rely on social engineering, it is important to ensure everyone in your organization knows how to spot suspicious communications and potential vulnerabilities around them.
- Training and Awareness: Educate employees on the significance of DNS security and the potential implications of lax practices, helping to mitigate risks from within.
- Due Diligence on DNS Configurations: Instill regular audits of DNS records within your IT teams, ensuring all records are accounted for and accurately reflect active services.
- Structured Decommissioning Protocols: As services change or retire, adopt stringent decommissioning processes that mandate review and removal of DNS records linked to obsolete resources.
2. Be Proactive With Attack Surface Monitoring
Combatting Dangling DNS requires a proactive approach, incorporating complete visibility and continuous monitoring of your digital infrastructure. Fortunately, technology has evolved to address this invisible threat head-on, and our Attack Surface Monitoring (ASM) solution stands at the forefront of preventative measures.
How Attack Surface Monitoring Helps You:
- Continuous Scanning: ASM continuously monitors DNS configurations to identify subdomains linked to non-existent services. This allows you to catch and rectify potential points of exploitation before they can be capitalized upon by hackers.
- Automated Alerts and Visibility: ASM provides automated alerts and continuous monitoring of your DNS settings and subdomains, promptly detecting any suspicious or unauthorized changes, including those pointing to non-existent destinations.
- Dangling DNS Indicators: The platform records these findings as specific “Issues,” such as “Dangling Resource Record,” detailing the problem and its severity. It then generates alerts to notify users of these misconfigurations, ensuring a rapid response to potential threats.
- Comprehensive Reporting: Get a full look into your attack surface with reports that show you every possible vulnerability, even ones you weren’t aware of.
Key Takeaways
Dangling DNS is a dangerous vulnerability that exploits oversight and inattention to wreak havoc on unsuspecting companies. Its potency lies in the stealthy control it gives hackers over legitimate brand assets. To protect your brand and digital spaces:
Cyber threats are continually evolving, but so are defenses. Through vigilance and targeted monitoring, thwarting Dangling DNS vulnerabilities is an achievable goal. Secure your digital brand identity today and maintain the confidence you’ve cultivated with your valued customers.
Need help with your Attack Surface?

For assistance with the details surrounding your particular attack surface, speak with one of our cybersecurity experts to learn more about how Attack Surface Monitoring could help you.