
As the internet continues to evolve, new security protocols emerge to help protect those who perform transactions over the web. One of these standards is the secure sockets layer (SSL) protocol which is used by millions of sites and IoT home networks worldwide. Additionally, security professionals recommend investing in SSL on the backend systems of enterprises, too.
Customer Facing SSL vs SSL on the Backend
You will know you are on an SSL protected website if you see the padlock icon at the top of your web browser beside the URL address.
Cybersecurity experts recommend that you double-check that a website has a valid SSL certificate installed before exchanging any kind of sensitive data with it. This can include passwords, social security numbers, or credit card data as part of an online checkout process.

But SSL is more than just a tool that browsers use to secure web requests. In fact, having SSL on the backend is a critical tool for enterprises to leverage.
Basics of SSL Encryption
At its core, the SSL protocol relies on a set of encryption algorithms. It encodes data sent from one endpoint so only the desired destination can open and interpret the associated information. If a hacker attempts to intercept that traffic, they will be unable to decode it. The same goes for SSL on the backend.
For SSL encryption to function properly, the enterprise who owns the destination server must have a valid certificate installed. These can be obtained through vendors like 101domain. 101domain partnered with Sectigo, the largest certificate authority worldwide, to link the certificates to your server’s domain name.
SSL transactions require a public key and a private key for encryption. The public key is stored directly in the certificate file and is automatically broadcast to all IP addresses on the same network. During the SSL handshake, the destination server uses the private key to encode and decode all data between two endpoints.

For an in-depth breakdown of SSL check out this Beginner’s Guide to SSL.
Types of SSL Certificates
To the average internet user, all SSL transactions seem to function in the same way. But in reality, vendors like 101domain offer a wide range of enterprise SSL certificate solutions for every need. SSL certificates typically involve an upfront cost along with renewal fees every 1-2 years.
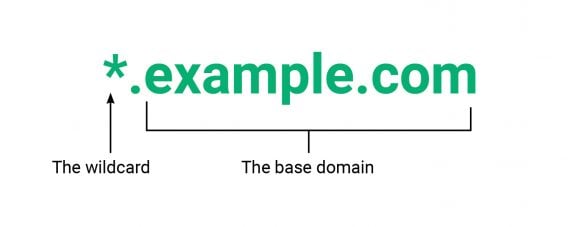
Wildcard SSL certificates are best for organizations with a complex IT architecture and various back-end systems that need securing. Wildcard allows you to encrypt your top-level domain as well as an unlimited number of subdomains you are using beneath it.
If vendors or third-party entities access your back-end systems, consider upgrading to an extended validation certificate.
EV adds an extra level of security by verifying your enterprise’s entity during every web session.
The Risk of Self-Signed Certificates
Due to the cost of annual certificate renewals, some enterprises may look for shortcuts to enable SSL on the backend. At a glance, self-signed certificates seem like an easy solution for internal and back-end systems but don’t be tempted. Because they don’t require involvement from a certificate authority, they are not as secure and anyone running a website can install them.
For this reason, SSL can only be trusted when a valid vendor certificate has been acquired at the domain level. Self-signed certificates are considered a security risk because there is no independent verification of their authenticity.
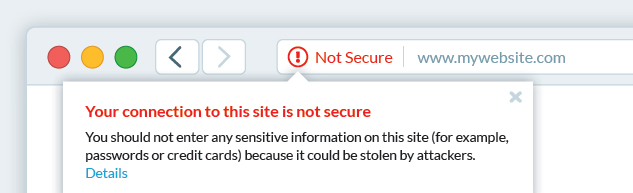
As a result, even when used only in an internal context, they will throw error messages to all users who try to connect through them.
Utilizing self-signed certificates is one of a variety of situations that could compromise your online safety. From a business perspective, a company that doesn’t have certified SSL certificates appears dodgy and is more vulnerable to cyberattacks. When it comes to doing business online, customer trust is the most important asset.
Another growing risk with self-signed certificates is that hackers have managed to subvert the encryption technology to hide malware in some cases. While not widely discussed yet, it’s worth being aware of these malware schemes that exist.
Internal Tools Require SSL on the backend
As mentioned earlier, a lot of the emphasis with SSL is placed on the browser interaction that external users see. However, it’s just as important to consider your policy for SSL on the backend. Even systems you don’t think people outside of your organization will ever use should be encrypted.
The cloud computing model is now standard practice for all enterprises who manage websites or web-based applications. Instead of running local servers and data centers, companies can rent computing power from a third-party provider. One reason why cloud hosting is the best type of hosting is because you only end up paying for what you use. In addition, one major benefit of cloud architectures is global reach. For example, with Cloudflare premium DNS, your back-end systems are spread around the world to provide the best level of performance.
However, if any server in the network lacks SSL protection, then it puts the entire enterprise at risk. Hackers can often infiltrate cloud systems without being detected by scanning for non-encrypted traffic at an internal level.
Any internal tool that is hosted through a software vendor should use end-to-end encryption. For example, project management systems like JIRA and chat applications like Slack contain sensitive information and should be protected. The same is true for email servers, which must use special port numbers when transmitting data over SSL connections.
The Bottom Line: SSL on the backend
SSL protection is one of several foundational steps to take to secure a website. In today’s world of online shopping and banking, any enterprise that lacks SSL certificates will be doomed to failure. Browsers will alert users to the fact that an SSL certificate is missing and urge them to not enter any sensitive data. Fortunately getting a website set up with an external-facing certificate is quite simple thanks to providers like 101domain.
But enterprises will leave themselves open to attack if they fail to extend SSL on the backend systems used internally. In a cloud environment, data is constantly traveling between different networks, offering plenty of opportunities for hackers to step in and intercept a transmission. The only way to keep those web exchanges private to an internal audience is to add SSL certificates at each end before the servers are put in a live production environment.