From the President & CEO’s desk
This post is a part of an ongoing series of conversations diving deep into how we can serve you and your organization’s needs. We hope you find this helpful!
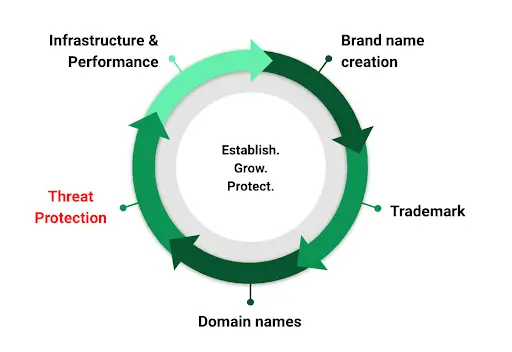
Decide on a name, register a trademark, and buy some domain names. This is a typical process when a brand is born. But what comes next as your venture grows?
It goes without saying that businesses face a constantly evolving cyber threat landscape as they operate and grow. Since the internet and networks were created, bad actors have always tried to take advantage of the system. This is a reality that makes growing a business even harder and more perilous than it needs to be.
We have a philosophy at 101domain we call Establish. Grow. Protect. to help guide our clients through this reality, avoidable pitfalls, and preventable cybersecurity events.
Businesses are great at establishing their brand in the public domain. After this however, we see many divergent paths businesses take to grow and protect their valuable turf in the digital domain, or not, for better and for worse.
If you haven’t grown your digital footprint beyond .COM, .NET, and .ORG, you’re vulnerable. Read my prior article here to understand how we can help you with domain names, brand protection and enforcement. The protection of domain names and brands goes hand in hand and many businesses have made the avoidable and costly mistake of treating domain names as an afterthought. We don’t want this to be you!
After establishing and growing your digital presence in the domain name space, we move on to help you Protect what you’ve built. If you’re like most modern businesses, you have one or many domain names in use, running a variety of applications, cloud services, websites, environments, and networks using many hostnames or sub-domains. As technology moves fast, these assets grow into the hundreds and even thousands or tens of thousands, quickly becoming complex and costly to manage.
In the digital realm, much like a physical estate, the greater the number of access points (doors and windows) in your digital estate, the more vulnerable entry points there are. Cybercriminals are sophisticated, and employ diverse tactics to breach security protocols, or lapses thereof, safeguarding these entry points, aiming to compromise sensitive assets and data. A sophisticated approach to cybersecurity is no longer a luxury but a necessity. They don’t have to blow up your budget and require vast resources though!
There is good news: a 101domain and Red Sift partnership
We have partnered with Red Sift, a leader in the cyber security threat detection and resiliency, to offer our clients a platform designed to reduce the cost and complexity of protecting your digital estate while providing triple threat protection: safeguarding your email, digital estate, and security certificates. This layered defense strategy ensures that businesses can proactively identify and mitigate risks as their technical operations grow, protecting their brand reputation, customers, and bottom line.
OnDMARC: Stopping Email Fraud and Boosting Deliverability
Email remains a primary target for cyberattacks. Phishing, spoofing, and Business Email Compromise (BEC) attacks exploit trust and familiarity to deceive recipients into revealing sensitive information or transferring funds. RedSift’s OnDMARC solution tackles this challenge head-on by implementing and automating DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC builds upon existing email authentication protocols, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), to provide a robust framework for verifying the legitimacy of email senders and blocking those attempting to send unauthorized email purporting to be you. OnDMARC demystifies DMARC, giving you real-time granular insight into your entire email sending operation across all of your domain names. Finally achieve and maintain p=reject or p=quarantine with real-time data to give you confidence that your emails are being received as intended.
Real world use cases:
- Banks use OnDMARC to prevent BEC attacks. By enforcing DMARC at the highest level (p=reject), banks and financial institutions ensure that only authorized senders can use its domain, blocking fraudulent emails from reaching their intended recipients. This proactive measure prevents financial losses and protects the institution’s reputation.
- E-commerce companies with high volume email marketing leverage OnDMARC to improve email deliverability. By authenticating their emails properly, these companies enhance their sender reputations, ensuring that legitimate marketing emails reach customers’ inboxes. This leads to increased customer engagement and higher conversion rates. We have seen email deliverability lifts of up to 40%!
- Complex businesses use OnDMARC for email visibility. Organizations with numerous marketing, technical, and communication teams frequently onboard email sending services without authorization or the necessary SPF and DMARC configuration. OnDMARC promptly notifies you to configure or reject emails, ensuring that your security posture is current and that your email campaigns successfully reach their intended audiences.
Attack Surface Monitoring: Proactively Identifying and Mitigating Cyber Threats
The modern business attack surface extends far beyond email. Your attack surface is the secure perimeter, doors and windows of your digital estate. Websites, applications, cloud infrastructure, and third-party integrations all present potential entry points for attackers.
RedSift’s Attack Surface Monitoring (ASM) solution provides continuous visibility and security assessment of your entire digital footprint. It scans all public-facing entry points, configurations, IP addresses and assets you may not even know exist. Catalog and organize all of your assets in a single pane of glass to see in near real-time and act quickly. Be alerted to vulnerabilities, fix issues, and re-scan the asset to verify your fix instantly. No longer pay and wait for full vulnerability scans days later. Help your staff work more efficiently.
Real world use cases:
- Healthcare providers use ASM to ensure compliance with HIPAA regulations. By identifying and mitigating vulnerabilities across their digital infrastructures, the providers safeguard sensitive patient data and avoid costly penalties for non-compliance.
- Technology companies use ASM to proactively manage risks associated with their rapidly evolving cloud infrastructures. By continuously monitoring changes and configurations across their cloud environments, the companies can quickly identify and remediate potential security gaps, ensuring the integrity and availability of their critical services.
- During security compliance audits, companies rely on ASM’s reporting and visibility capabilities to expedite evidence generation. Auditors frequently request a wide range of reports, screenshots, and demonstrations to ensure compliance. ASM securely provides this visibility, saving time, alleviating frustrations for all parties involved, and eliminating the need for various traditional and custom-built tools and scripts previously used for this purpose.
Certificate Monitoring: Ensuring the Security and Integrity of SSL/TLS Certificates
SSL/TLS certificates are fundamental for establishing secure communication channels and protecting data transmitted online. Expired or compromised certificates can lead to website outages, data breaches, and erosion of customer trust. RedSift’s Certificate Monitoring solution offers real-time discovery, monitoring, and management of all certificates associated with your domains and subdomains, used externally and internally and even with your vendors.
Real world use cases:
- Online retailers use Certificate Monitoring to prevent website downtime and maintain customer confidence. By receiving proactive alerts for upcoming expirations, retailers ensure seamless certificate renewals, avoiding service interruptions and potential revenue loss.
- Financial institutions use Certificate Monitoring to protect against man-in-the-middle attacks. By continuously monitoring for certificate anomalies, institutions can quickly detect and respond to compromised certificates, preventing attackers from intercepting sensitive customer data.
- Companies find unauthorized SSL Certificates posing as legitimate. Proactively identify unauthorized SSL certificates that pose as your legitimate website. These fraudulent certificates are typically used in phishing attacks, attempting to trick customers into providing sensitive information such as login credentials and financial details.
The Power of Integration and a Comprehensive Approach partnering with 101domain and RedSift
OnDMARC, ASM and Certificate Monitoring seamlessly integrate with your existing systems, including SIEM and SOAR platforms, cloud providers, and email sending services, allowing for efficient workflow automation and centralized management of security operations. There is no interruption to your operations or downtime.
101domain’s dedicated solutions engineers and customer success team are committed to helping our clients maximize the value of their cybersecurity investments. From initial onboarding and implementation to ongoing support and strategic guidance, we provide the expertise and resources needed to achieve a robust security posture and are here when you need us.
By adopting our triple threat protection approach, businesses can establish a proactive, cost-effective and comprehensive cybersecurity strategy that protects against email fraud, safeguards systems and attack surfaces from a vast array of threats, and ensures the integrity of security certificates across the organization. This integrated approach minimizes risk, fosters customer trust, and empowers businesses to work smarter, not harder. thrive in the digital age.
Start reaping the benefits of triple threat protection today. Contact us for a free and thorough consultation.
Sincerely,
Anthony Beltran
President CEO
101domain.com
