
Cybercrime has become more costly than it ever has been before. With businesses collectively losing over $1 trillion in 2020 globally as a result of cybercrime, criminals are finding more ways to attack businesses in unprecedented ways. Not being aware of how or where these attacks are coming from will only leave your business more at risk of becoming the next victim.
Phishing attacks, endpoint security vulnerabilities, ransomware, and insider attacks are among the biggest threats businesses faced in 2020. But using look-alike domains to impersonate authentic businesses was one of the most effective and yet simplest strategies used by cybercriminals to commit fraud and scams. To help you avoid falling preyto look-alike domains, this article will explore what this attack looks like, how to spot it, and how to protect your business against it.
What is a look-alike domain?
To fully understand what a look-alike domain is and how it may impact you, it’s important to cover the basics of what a domain is. In short, during the early days of the internet, domains were introduced to essentially be a name-tag for a website – an established unique identity for a website that represents its IP address in an easy-to-remember form.
Every website on the internet has a unique domain. Choosing and purchasing a new domain is one of the many steps one has to go through when setting up a new website or online store. However, it’s also one of the biggest factors that get exploited by hackers.
As you may have guessed by the name, a look-alike domain is a domain that is very similar to the legitimate domain of an authorized website. However, there are one or more small differences that are almost impossible to spot at a glance. Scammers purchase these similar domains in the hope that people will accidentally visit their site instead of yours and enter sensitive information that they can steal.
How are look-alike domains created?
There are three main parts to a domain: the subdomain, the top-level domain, and the second-level domain.
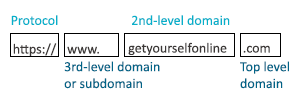
The subdomain is where you would see writing such as “www.” or “https://”. It essentially registers a website to a certain section or category of the internet. The top-level domain is the “.com”, “.net”, or another variant. Finally, the second-level domain is the actual domain name combined with the top-level domain.
When cybercriminals are looking to create look-alike domains, they will target one or more of these parts to alter. One of the most common ways they do this is by taking a “.com” website and either changing the extension from “.com” to another variant such as “.org”. With over 1,600 different domain extensions, it’s an easy strategy for hackers to introduce an international domain code to create a top-level look-alike domain such as “.com.eg” to the end.
Scammers may also omit one or two letters from the real domain, known as an omission look-alike, or add a hyphen in between one or more words. The reason why this scam works is because we don’t necessarily fully read a URL when we click on it. In fact, our brains scan it to see if it is accurate at a glance and, if so, you are more likely to click through to the site.
And considering the fact that there are over 366.8 million domain names registered on the internet, it may seem impossible to protect yourself against these attacks. Fortunately, there are a few viable strategies and precautions you can implement.

How can I protect myself against a look-alike domain?
There’s no telling the extent of what may happen should you fall victim to a look-alike domain scam. You may lose credit card information, confidential business information, or fall victim to other hacking activities. The average small business loses 5% of its total revenue each year just due to fraudulent behavior. Due to these potential consequences, it’s critical to be aware of what you can do to avoid this scam.
As an average internet user, the best way to avoid falling victim to a look-alike scam is to double-check every URL link. Rather than typing links from memory, consider using Google and recognizing the correct site from the pages listed highest on the search engine. This will make you less prone to a typing mistake that may lead you to a fraudulent site.
As a website owner, your response to an attack must be swift and decisive to protect your website, reputation, and customers. Consumers get angry with both look-alike websites and the authentic brand when they are scammed, and these fraudulent websites can seriously hurt your reputation.
You should always offer a hosted help desk tool that integrates with your domain name in your business website to help provide support to customers. However, you can also attempt to prevent hackers from creating look-alike domains at the point of registering your business. A domain registrar is an authentic organization that grabs similar domains for domain owners, and it’s a cost-effective way to stop other people and hackers from getting their hands on similar domains.
For larger organizations, there are policies in place, such as the Digital Millennium Copyright Act 1998, that protects your digital assets with copyright laws. In the United States, you can request a site be taken down under this act and the service provider will have three days to do so.
Instead, choose a host that offers exceptional customer support and privacy protection that will cover you in the case of a look-alike domain attack. According to London-based web developer Alex Williams of Hosting Data, web hosting providers should also provide assistance in identifying and removing look-alike domains with the correct documents and evidence. When selecting a web and hosting service provider, you should look for a company that offers advanced security features such as SSL certificates, domain locking, IP lock and logging, and monitoring and enforcement services.
One final strategy you can implement is to simply send out a company email to your employees and request that they block the fraudulent URL so that sensitive information is not leaked.
Taking the necessary steps to secure your business in the digital age
Cybercriminals will always be around for as long as the internet exists, but that doesn’t mean you should accept the fact that your business falls victim to a cyberattack. By becoming knowledgeable about the different scams and fraudulent activity that may fall into your path, you can put the necessary steps in place to stay better protected.
Following simple and necessary steps such as verifying your website and putting the essential privacy protections in place such as premium SSL certificates, which are up to 97% more secure than basic encryption-only DV websites, can make all the difference when hackers are looking to target your domain for their next scam.