
In the last decade, web development has gone from a niche specialty to a common skill set among technical workers. As a result, many companies now choose to outsource their coding projects to freelancers or offshore units as a way of reducing costs and complexity.
The Security Trade-Off: Outside Web Developers
However, employing a team of outside web developers does increase security concerns. Since the workers are not located in the same facility, they will need to access internal tools over the open Internet. This can leave an organization exposed to attack even if the remote worker has the best of intentions.
In this article, we’ll cover the key security practices to focus on when setting up a new project that involves one or more outside web developers.
1. Look for the Right Outside Web Developers
The first mistake that many companies make is to hire freelance or contract outside web developers based solely on their resume or skill list. If you know that a project is going to be written in the Java programming language with an Oracle database back-end, then it seems logical to pursue a candidate who specializes in those areas.
However, you need to consider the person’s overall profile before trusting them with major responsibilities. Specifically, you want to see a full portfolio from the candidate that showcases their coding work on similar projects. Cybersecurity experts from within your organization should review these samples to help verify that the individual follows best practices.
2. Choose One Communication Tool
Another place where organizations can run into trouble is with data sharing between their internal staff and freelancers. This exchange has to happen over the open Internet, which introduces a significant amount of risk. Consider a situation where your outside web developers prefer to work in their personal Dropbox accounts. Now you, as the project leader, need to determine whether that is safe or not.
As a general rule, it’s smart to have your outside developers funnel all communications and data transfers through a single route. This can be as simple as secure DNS with Cloudflare or more complex like dedicated Slack channels, which have security built-in by default.
Either way, by having all work focused in a single area it becomes easier to track and audit in the future. This is especially valuable if you are paying the contractor based on when certain tasks are completed.
3. Use the Principle of Least Privilege
When hiring outside web developers, you want to remove as many roadblocks as possible so those individual can do their work as efficiently as possible. For that reason, it can be tempting to provide them with full administrative access to the parts of the network, servers, and applications that they will be working on as part of the project.
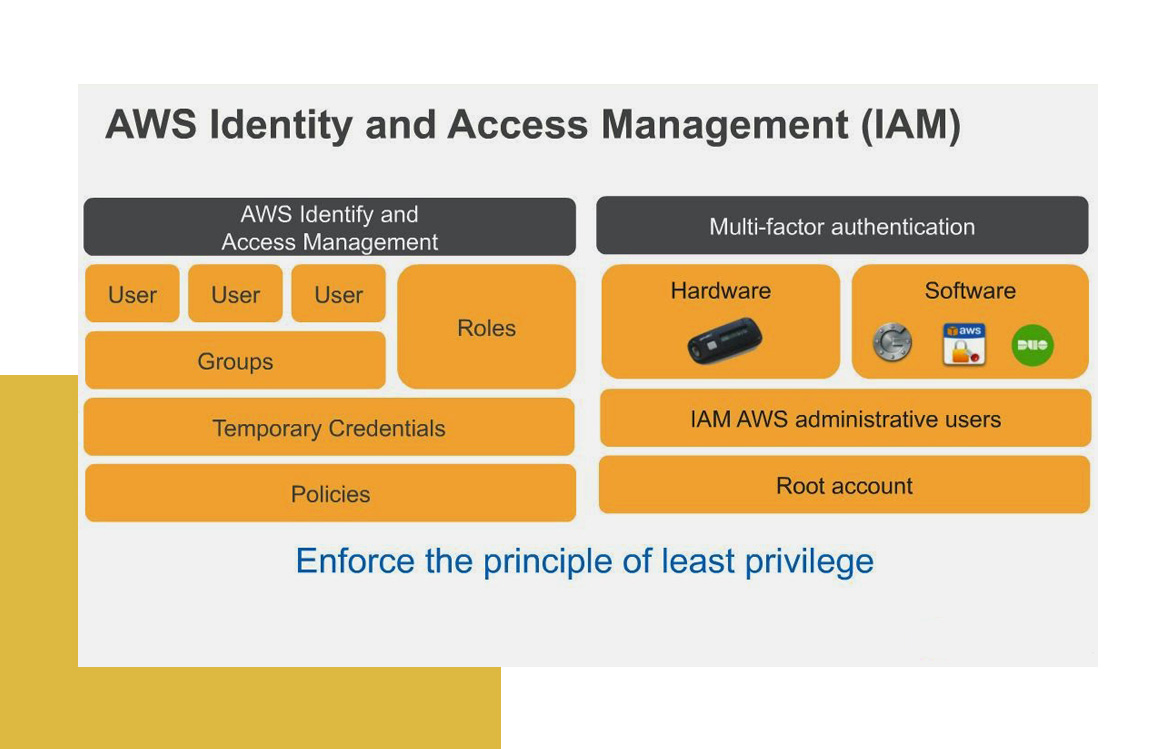
However, this is a serious mistake and a giant cybersecurity risk. Giving admin access to too many individuals is often how cyberattacks and data breaches can occur. Instead, you should follow something known as the Principle of Least Privilege (POLP). It states that each person working within a system should only be granted access permissions at the minimum level needed to complete their job.
As seen at 101domain…
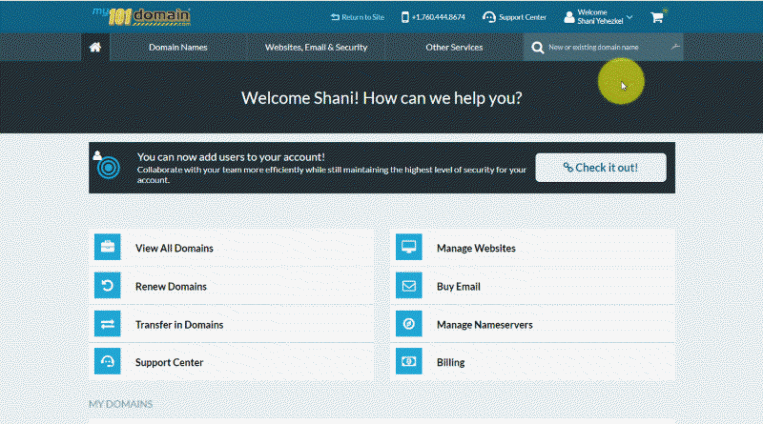
Account owners can create role-based users to help you and your team collaborate more efficiently while still maintaining the highest level of security you expect with your 101domain account.
Each user will have their own username and password to log in to the account with tools that are personalized for their specific role. Account users are the best way to give your team members including outside web developers access to the tools they need, and none that they don’t.
In the era of cloud hosting, when applications are being run through hosting providers and shared data centers, controlling your identity and access management (IAM) protocols is critical. Cloud computing demands a robust security system that allows you to set granular permissions for every user and then audit all related activities.
4. Manage Deployments Internally
Working with remote employees presents a communication challenge, as you cannot speak with freelancers in person and sometimes meaning can be lost in translation. In a worst-case scenario, a contractor could misinterpret a request and end up creating a new issue on a live application that takes down a whole website.
To help protect against that, organizations should employ a mature development cycle that limits outside access to live systems. The standard workflow includes three dedicated environments: development, stage, and production. Production houses the live application, stage houses the latest changes that have been approved by the quality assurance team, and development is used as the sandbox for coders to work.
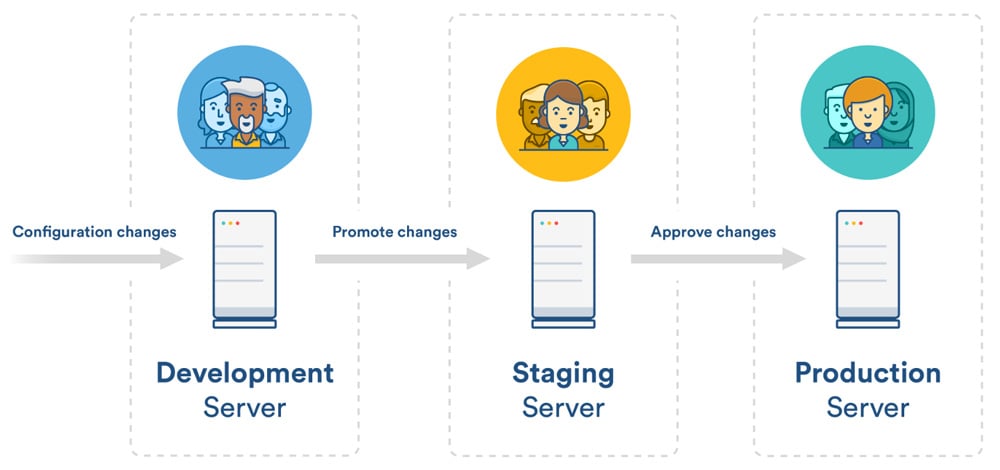
In general, outside workers should only ever have access to the development environment for security reasons. The organization running the project should have an in-house QA team responsible for testing all new code and then promoting changes up to the stage and production systems.
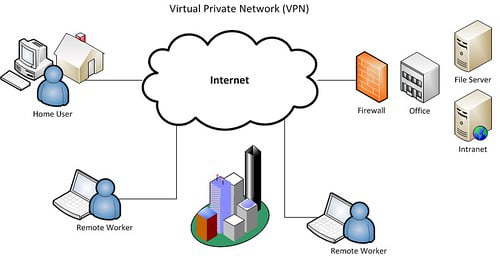
5. Mandate the Outside Web Developers VPN Usage
Even if you take every precaution when setting up a remote developer’s access to your Internet systems, there is still a chance that data could be exposed during the lifecycle of the project. The highest risk comes when a freelancer is working on a public wi-fi network, where hackers could be intercepting data through a compromised router or switch.
To be safe, you should require that all outside web developers connect to a virtual private network (VPN) client before accessing any internal resources or sending critical data over the internet. The best VPN services today offer multiple security protocols, which encrypt web traffic on your device and make it impossible for hackers to decode and steal information.
VPNs also require a second layer of authentication, which can help to protect an organization’s data in case the freelancer’s computer is lost or stolen. Other individuals will not be able to connect to servers or databases unless they first log in through the VPN with an approved username and password.
The Bottom Line for Employing Outside Web Developers
Companies can reap significant benefits by utilizing outside web developers. But there is a trade-off, as more focus must be put on the security of internal and external systems. A single point of failure can result in disaster for the organization.
Fortunately, best practices have emerged to help make third-party development a safer and more streamlined process. Nowadays, an outside developer can feel like a true member of the team. They can make serious contributions to a project or application without putting the company’s internal resources in jeopardy.